Nslookup (name server lookup) is a command-line tool that is used to diagnose and validate DNS servers and records, and to find name resolution problems in the DNS subsystem. The nslookup tool was originally developed as a part of the BIND package and ported to Windows by Microsoft. Nslookup is currently a built-in tool in all supported versions of Windows.
How to Use Nslookup to Check DNS Records?
Using the nslookup utility, you can determine the IP address of any server by its DNS name, perform the reverse DNS lookup, and get information about the various DNS records for a specific domain name.
When running, Nslookup sends queries to the DNS server that is specified in your network connection settings. This address is considered the default (preferred) DNS server. The user can specify the address of any other available DNS server. As a result, all subsequent DNS requests will be sent to it.
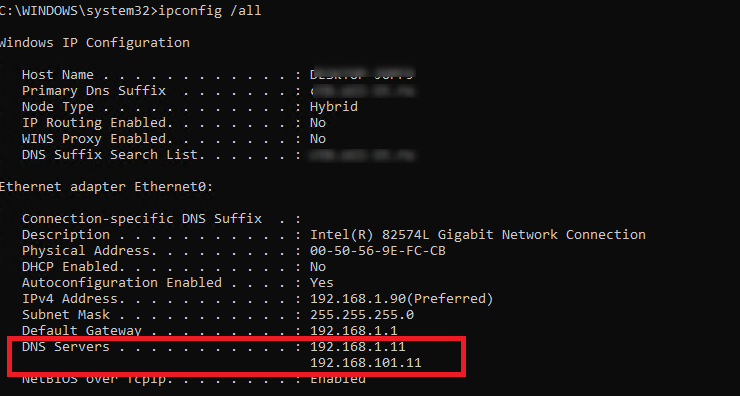
You can view or change your preferred and alternative DNS server IP addresses in the network connection properties.

Or you can get your DNS server setting from the CLI prompt using the ipconfig command:
ipconfig /all
You can use the nslookup tool in interactive or non-interactive mode.
To run a DNS query using nslookup tool in non-interactive mode, open a Command prompt, and run the command:
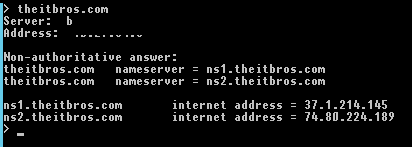
Nslookup theitbros.com

In this example, we requested the IP address of theitbros.com domain. The nslookup utility queries the DNS server (it is specified in the Server line) and it returned that this name matches the IP address 37.1.214.145 (A and AAAA records are shown by default).
This response indicates that your DNS server is available, works properly, and processes requests for resolving DNS names.
If you received such an answer:
Server: dns1.contoso.com
Address: хх.хх.хх.хх
*** dns1.contoso.com can’t find theitbros.com: Non-existent domain
This means that no entries were found for this domain name on the DNS server.
If your DNS server is unavailable or not responding, you will receive a DNS request timed out error.

In this case, check if you have specified the correct DNS server address and whether there is a problem with the network connection from the IS provider.
The Non-authoritative answer means that the DNS server that executed the request is not the owner of the theitbros.com zone (there are no records about this domain in its database) and to perform name resolution a recursive query to another DNS server was used.
You can enable and disable the recursive nslookup mode using the commands (by default, recursive DNS queries are enabled):
set recurse
set norecurse
You can access an authoritative DNS server by specifying its address directly in the parameters of the nslookup utility. For example, to resolve a name on the authoritative DNS server (that contains this domain) use the command:
Nslookup theitbros.com ns1.theitbros.com
When you run nslookup without parameters, the utility switches to the interactive mode. In this mode, you can execute various commands. A complete list of available internal commands of the nslookup utility can be displayed by typing a question.
Tip. Note that nslookup commands are case sensitive.

To close the interactive nslookup session, type exit and press Enter.
To find the DNS servers that are responsible for a specific domain (Name Server authoritative servers), run the following commands:
set query=ns
theitbros.com
You can perform reverse lookups (get DNS name by IP address). Just type the IP address in the nslookup interactive prompt and press Enter.

Using Nslookup to Get Different DNS Record Types
The default nslookup resource records type is A and AAAA, but you can use different types of resource records:
- A
- ANY
- CNAME
- GID
- HINFO:
- MB
- MG
- MINF
- MR
- MX
- NS
- PTR
- SOA
- TXT
- UID
- UINFO
- WKS
You can set specific record types to lookup using the nslookup parameter:
-type=<record_type>
For example, to list all mail servers configured for a specific domain (MX, Mail eXchange records), run the command:
nslookup -type=mx theitbros.com

Non-authoritative answer:
theitbros.com MX preference = 10, mail exchanger = mail.theitbros.com
theitbros.com MX preference = 20, mail exchanger = mail.theitbros.com
mail.theitbros.com internet address = 37.1.214.145
mail.theitbros.com internet address = 37.1.214.145
As you can see, this domain has 2 MX records with priorities 10 and 20 (the lower the number, the higher the priority of the MX address). If you don’t see MX records, they probably just aren’t configured for that domain.
To list all DNS records in the domain zone, run the command:
nslookup -type=any theitbros.com
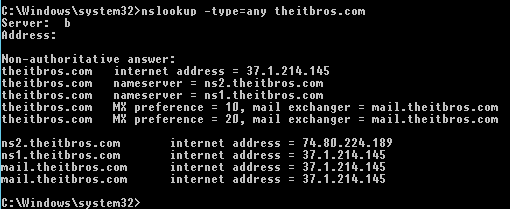
Non-authoritative answer:
theitbros.com internet address = 37.1.214.145
theitbros.com nameserver = ns2.theitbros.com
theitbros.com nameserver = ns1.theitbros.com
theitbros.com MX preference = 10, mail exchanger = mail.theitbros.com
theitbros.com MX preference = 20, mail exchanger = mail.theitbros.com
ns2.theitbros.com internet address = 74.80.224.189
ns1.theitbros.com internet address = 37.1.214.145
mail.theitbros.com internet address = 37.1.214.145
mail.theitbros.com internet address = 37.1.214.145
To get the SOA record (Start of Authority – start DNS zone record, which contains information about the domain zone, its administrator’s address, serial number, etc.), use the option -type=soa:
nslookup -type=soa theitbros.com
theitbros.com
primary name server = pdns1.registrar-servers.com
responsible mail addr = hostmaster.registrar-servers.com
serial = 1601449549
refresh = 43200 (12 hours)
retry = 3600 (1 hour)
expire = 604800 (7 days)
default TTL = 3601 (1 hour 1 sec)
pdns1.registrar-servers.com internet address = 156.154.130.200
pdns1.registrar-servers.com AAAA IPv6 address = 2610:a1:1022::200

- primary name server;
- responsible mail addr — domain administrator email address (This email address is being protected from spambots. You need JavaScript enabled to view it.). Since the @ symbol in the zone description has its own meaning, it is replaced by a dot in this field);
- serial — the serial number of the zone file, used to record changes. The following format is usually used: YYYYMMDDHH;
- refresh — the period of time (in seconds) after which the secondary DNS server will send a request to the primary one to check if the serial number has changed;
- retry — specifies the interval for reconnecting to the primary DNS server if for some reason it was unable to respond to the request;
- expire — specifies how long the DNS cache is kept by the secondary DNS server, after which it will be considered expired;
- default TTL — “Time to Live” seconds. Refers to how long your DNS settings must be cached before they are automatically refreshed.
If you want to list the TXT records of a domain (for example, when viewing SPF settings), run the command:
nslookup -type=TXT theitbros.com
The debug option allows you to get additional information contained in the headers of client DNS requests and server responses (lifetime, flags, record types, etc.):
set debug

You can view the current values for all specified nslookup options with the command:
> set all
Default Server: ns1.theitbros.com
Address: 192.168.1.11
Set options:
nodebug
defname
search
recurse
nod2
novc
noignoretc
port=53
type=A+AAAA
class=IN
timeout=2
retry=1
root=A.ROOT-SERVERS.NET.
domain=xxx
MSxfr
IXFRversion=1
srchlist=xxx

By default, DNS servers listen on UDP port 53, but you can specify a different port number if necessary using the -port option:
nslookup port 56 theitbros.com
or interactively:
set port = 56
You can change the interval to wait for a response from the DNS server. This is usually necessary on slow or unstable network links. By default, if no response comes within 5 seconds, the request is repeated, increasing the waiting time by two times. But you can manually set this value in seconds using the -timeout option:
nslookup -timeout=10 theitbros.com
So, in this article, we covered the basics of working with the nslookup command on Windows.
If the directory is removed from IIS, but remains in AD, you must first remove the directory from AD using the Remove-XXXVirtualDirectory cmdlet (where XXX is the name of the directory: ECP, OWA, etc.).

If the directory is still in IIS but is not present in the Active Directory configuration, you must remove it from the IIS configuration. To do this, we need the Metabase Explorer tool from the IIS 6 Resource Kit (requires Net Framework 3.5 Feature).
Launch IIS Metabase Explorer, go to Exchange > LM > W3SVC > 1 > ROOT. Delete the directory you want by right-clicking on it and choosing Delete.

Restart IIS:
iisreset /force
Now attempt to create the virtual directory again using the New-EcpVirtualDirectory, New-OwaVirtualDirectory, or New-WebApplication cmdlets

 English
English
 中文
中文 




















